Reverse Engineering
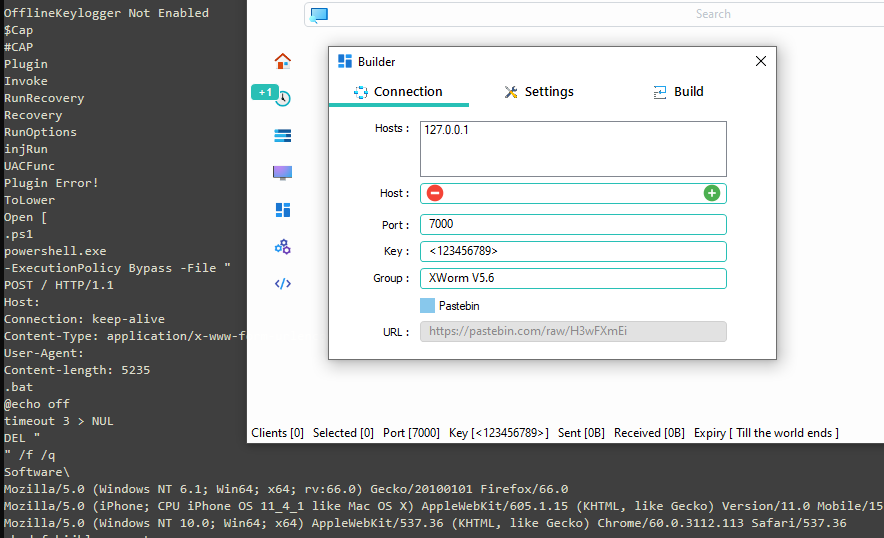
xWorm Extractor - Extracting Configs Without a Sandbox
Extracting xWorm configs from the binary without the requirement of running it.

Reverse Engineering
Extracting xWorm configs from the binary without the requirement of running it.
C2Hunt
Looking into default Teamserver profiles and how lack of modification can leave Havoc Teamservers exposed online.
fraud
We pick up something from the trash pile and figure out its phish kit family! Giving birth to a hunt query to detect Contiinued phish kit portals using URLScan

FOFA
Hunting for fraud sites from no formal information. Pivoting into exposing Australian MyGov portal fraud and shining a spotlight on a certain Russian host; home to big phishes

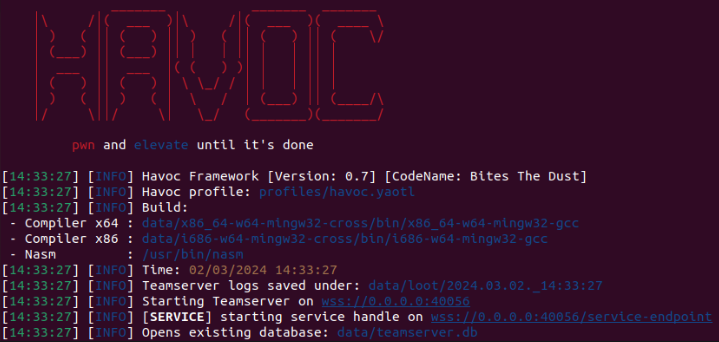
C2Hunt
How do we hunt for the Havoc C2 framework? A slight OPSEC slip up might be all that is needed

Hunting
How we can use FOFA to identify indicators to hunt for Sliver C2 instances running multiplayer

GitHub - secsi/QRaider: A QRCode dumperA QRCode dumper. Contribute to secsi/QRaider development by creating an account on GitHub.GitHubsecsi Leading on from this previous post about using lock keys to allow keyboard communications [https://blog.badoosb.com/a-badusb-for-dlp/]. We are going to construct a QR reader, with associated

AutoPwny
GitHub - secsi/AutoPwny: Think “BadUSB” but with two-way communicationThink “BadUSB” but with two-way communication. Contribute to secsi/AutoPwny development by creating an account on GitHub.GitHubsecsi Leading on from this previous article. We are going to utilise lock keys to get command confirmation from HID keyboard input. Sounds crazy.
For those who havent heard of them yet; BADUsb's are effectively hardcoded boards which, when connected to a computer, declare themselves as a class akin to a keyboard. Because they are a keyboard, they dont have any methods of communication. As such, when payloads launch, they are effectively