Fluid Fraud Hunting - Getting Something From Nothing
Hunting for fraud sites from no formal information. Pivoting into exposing Australian MyGov portal fraud and shining a spotlight on a certain Russian host; home to big phishes

When given an IOC to work with, its fairly directional; in the sense that there is a flow to pivoting and building out surrounding information. However, if you have nothing to hunt for... where can you go and find something no one else is looking at yet? More importantly... without having to pay for the pleasure of doing so.
The concept of this style of hunting is basically like dumpster diving. Jump in the cesspool, and keep pivoting for bigger game.
So step one... catch a small fish

Step X.... catch the big fish

Spoiler alert, this starts small, but with fluid pivoting, we end up having visibility of a relatively large host of scams and fraud.
Finding Some Bad Domains
Finding treasure in the trash
A nice way to get involved is to go look at newly registered domains. Whoisds.com offer (for free) a sample of 100k newly registered domain names. Im uncertain of the time of the file uploads, but you can get the last 4 days worth here:

This now opens up avenues to look for typo squats and fraud campaigns. For example I only need to look at line 51 for the file I downloaded to see a popular adult site typo squat.
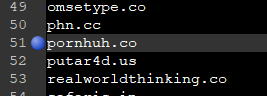
Maybe its a porn site for people with a fetish for confusion?

One particular method I'm fond of, is to regex search the file. This is the main reason I utilise notepad++ due to its regex search feature. below are some examples of patterns I like looking for for quick wins.
TLD Spoofing
gov\.
-co-uk.
-com\.
Login Portal Spoofs
login
portal
Big Brands
disney
netflix
prime
Other Keywords/Patterns Of Interest
refund
account
verification
\d{6,} (6 digits or more always seems to flag domains of interest. Look for patterns between them as some might be DGAs)
[a-f0-9]{16,} (finds all domains with a potential hash involved, also a sign of a potential DGA)
TLD Spoofing
gov.
-co-uk.
-com.
Login Portal Spoofs
login
portal
Big Brands
disney
netflix
prime
Other Keywords/Patterns Of Interest
refund
account
verification
\d{6,}
[a-f0-9]{16,}
To explain the two patterns at the end there. They look for 6+ sequential digits, normally standard domains go up to 4 (the year) and rarely do companies have a requirement for more than this.
The "[a-f0-9]{16,}" finds all domains with a potential hash involved, also a sign of a potential DGA.
Now we compile our list into a super regex OR pattern. Important to note we wont catch many typo squats of brand names, but you can figure this one out at a later point in time.
Regex pattern: (gov.|-co-uk.|-com.|login|portal|disney|netflix|prime|refund|account|verification)
I hit search for the entire file and get 305 hits. Much easier to sift through than 100k.

Picking the Small Game
Australian ATO Fraud
One that peaks the interest is "portalgov-ato[.]org" which I look at and think may be relating to the Australian ATO fraud.

Pivot and swap to URL scan....

Cloudflare... makes it awkward for proxies to scan these sites. So loading up our VM (just in case of drive-bys) we navigate through to the domain via our VPN...
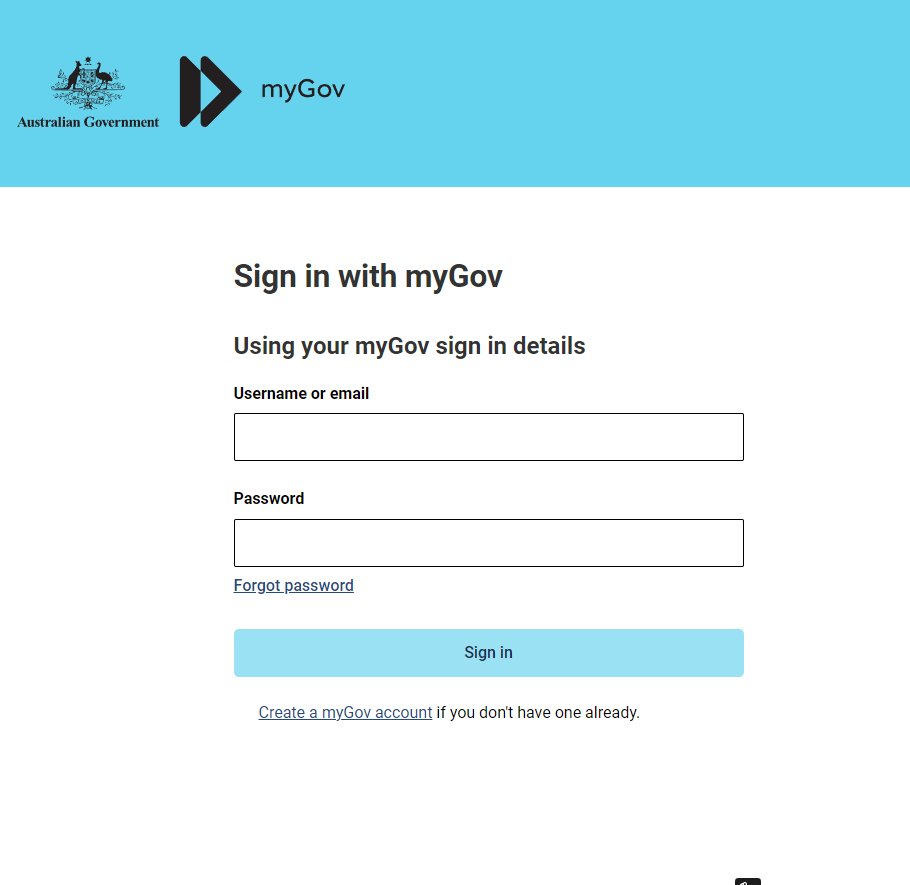
Snap! Australian ATO fraud as expected.
So they're behind Cloudflare, cant find any trace of them on FOFA. I can see the cert registration in Censys and CRT.sh but not where it is. Dead end it seems.
Fluid Pivot- HTML of the Phish Page
Using a small fish... to find more fish
So I'm going to pivot out and see how much ATO fraud I can uncover from this one phish page.
The pages title tags are set to "Sign in with myGov - myGov"
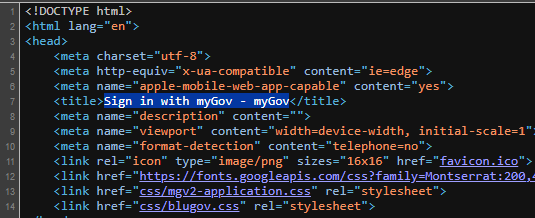
However the OFFICAL sign in page is set as follows:
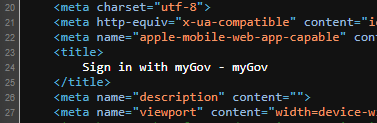
Note the extra lines. There is effectively white space in the official page, which means if we slip into FOFA and search for ">Sign in with myGov - myGov<"...
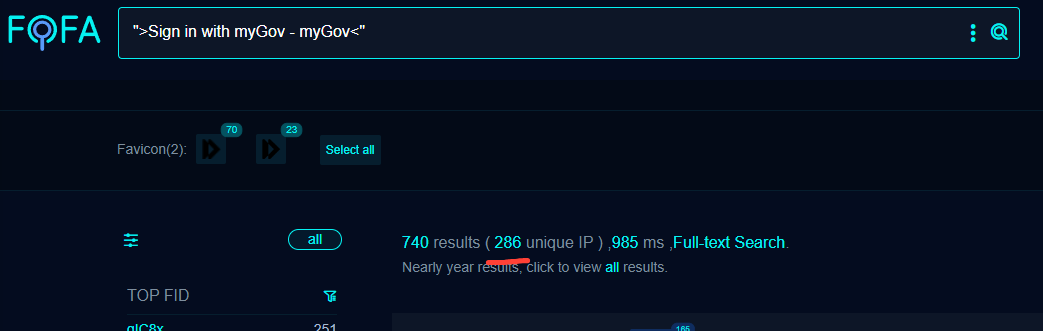
286 IPs matching this criteria. Most of the first page is Digital Ocean and AS-Choopa. Some example domains:
my-gov-revenue[.]info
mygovnswau[.]com
uoxat[.]online
profile-security[.]com (old domain)
Pivoting off of the server type with fewest results (Lightspeed), reveals a lot of activity from the same IP.
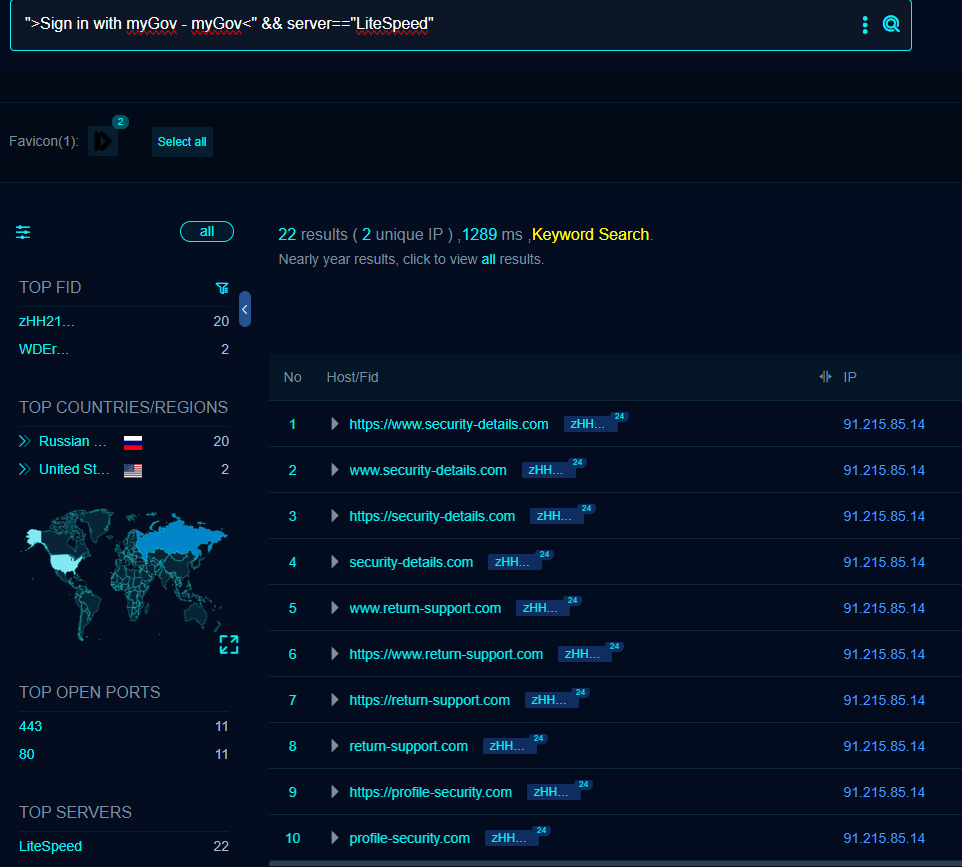
Last active on the 31st August last year, however, lets just have a quick look and see if that IP is still going:
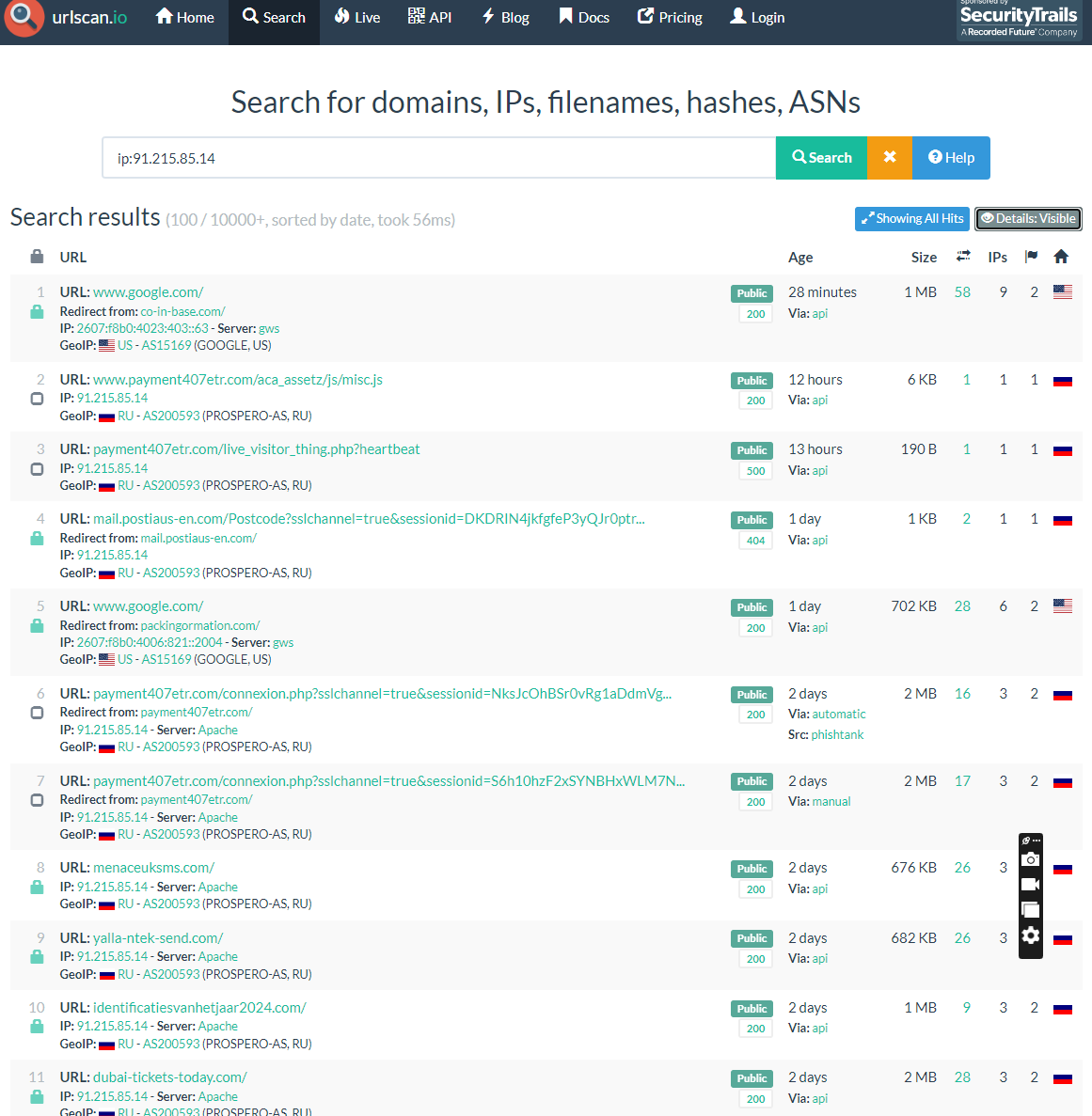
Jackpot. An active IP producing many scam pages it seems. Virus Total seems oblivious to this...

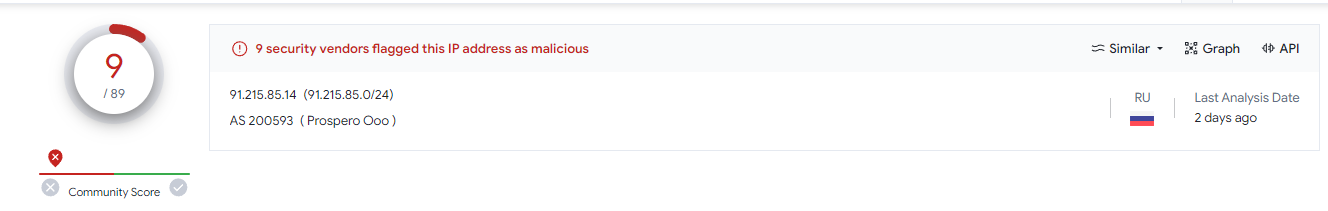
So I'm going to stop this one here. All the above is to say, even if you don't have an IOC to start with. Poke around long enough and you'll find some good leads. In this case we:
Found a suspicious URL,
confirmed it was fraud,
pivoted on the HTML used in the campaign,
unveiled further fraud,
Found a Russian IP hosting a whole array of fraud domains.
Detections and Hunt Rules
Pretty good indicators to start hunting with
As with any form of hunt, its good to keep track of indicators you've found, so you can pick up later on and work on them more surrounding detections of specific actors and/or kits in use.
Name: URLScan - Australia MyGov Spoof
Query: page.title:"Sign in with myGov - myGov" AND NOT page.domain:my.gov.au [1]
Name: URLScan - Australia MyGov Spoof (hash of logo in use)
Query: hash:954aa858b3bffb8511bc41bc88b07d2b24597c37faf522550e26c9aa3b0d220d AND NOT page.domain:my.gov.au [3]
Name: FOFA - Australia MyGov Spoof
Query: ">Sign in with myGov - myGov<" [2]
Name: URLScan - Potential MyGov Actor Identification - Usage of same CSS file
Query: hash:ea35b47cc661720657da76cf7ac5e8ce4a9d5774326b4b5f85b401726c27f906
[1] https://urlscan.io/search/#page.title%3A%22Sign%20in%20with%20myGov%20-%20myGov%22%20AND%20NOT%20page.domain%3Amy.gov.au
[2] https://en.fofa.info/result?qbase64=Ij5TaWduIGluIHdpdGggbXlHb3YgLSBteUdvdjwi
[3] https://urlscan.io/search/#hash%3A954aa858b3bffb8511bc41bc88b07d2b24597c37faf522550e26c9aa3b0d220d%20AND%20NOT%20page.domain%3Amy.gov.au
[4] https://urlscan.io/search/#hash%3Aea35b47cc661720657da76cf7ac5e8ce4a9d5774326b4b5f85b401726c27f906