Hunting For Havoc C2s
How do we hunt for the Havoc C2 framework? A slight OPSEC slip up might be all that is needed

Havoc is a fairly popular C2 framework used by Red Teams and adversaries. Effectively allowing multiple adversaries to collaborate on the same attack path simultaneously.
Looks and operates fairly similarly to Cobalt Strike on the surface.
So how can we hunt for this?

Searching through the repository for Havoc for items such as certificates, default templates, HTTP response configurations (including redirects etc). I stumbled upon this:
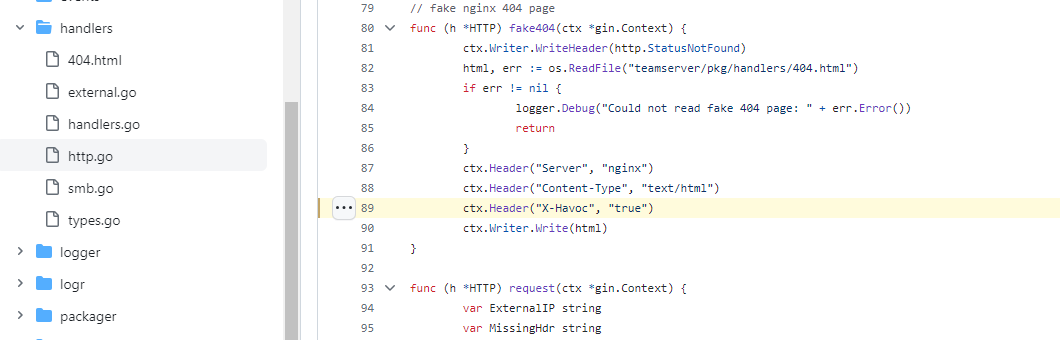
Could it be that the default code base for Havoc.... actually tells the world that its Havoc? Well, yes, and I don't believe the developers have done anything crazy stupid here, anymore than EvilGinx adding the X-Evilginx header by default.
So not a developer fail, but definitely an OPSEC fail. Why would anyone go to the effort of editing out this particular indicator?!

How many fall for this though?


Pivoting off this search into one of the IPs we can see Havocs response header is only included within a direct request to the port. Should a host header be used (in this case cloudns.ch) a separate header is received. In this particular instance its a 301 redirect to Google.com, presumably as its been configured to do so if an acceptable user agent is not present.

In short; if you suspect a domain of being a C2, by getting the host header of the IP directly, it is likely that the software has not been configured appropriately.