Havoc - Part Two - Finding Havoc C2 Team Servers
Looking into default Teamserver profiles and how lack of modification can leave Havoc Teamservers exposed online.
In the previous Havoc hunt post we went over a basic OPSEC fail, whereby default scripts add tags to the HTML response identifying it as a Havoc server using "X-Havoc: true". In theory this is easily overcome by a modification of the profile itself.
Moving on; I decided to play with Havoc directly and see if there was any additional default profile behaviours we can possibly pick up on. Specifically under the idea of enumerating the services and attempting to be able to identify it in the wild.
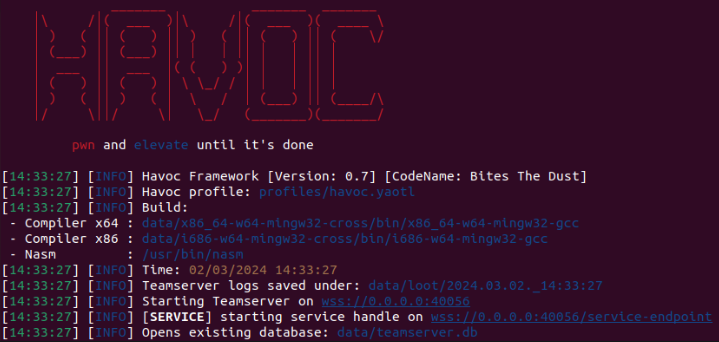
Once Havoc is installed, we can launch the Teamserver (again with the default profile supplied...
By default this wants to listen on 40056. This is kind of irrelevant as port numbers can obviously be adjusted. What other indicators can we find?
Well if we navigate to the port directly via a web browser, we get a certificate:
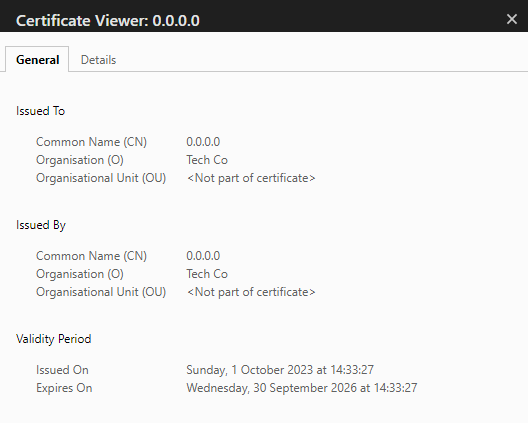
The "Tech Co" is of interest. I didn't add this at all prior to launching the team server. But the Common Name is also a fairly odd selection.

One thing to note is that I believe the org name is randomised; but not the common name. So looking through the Github repo we find a nice little reference to it:
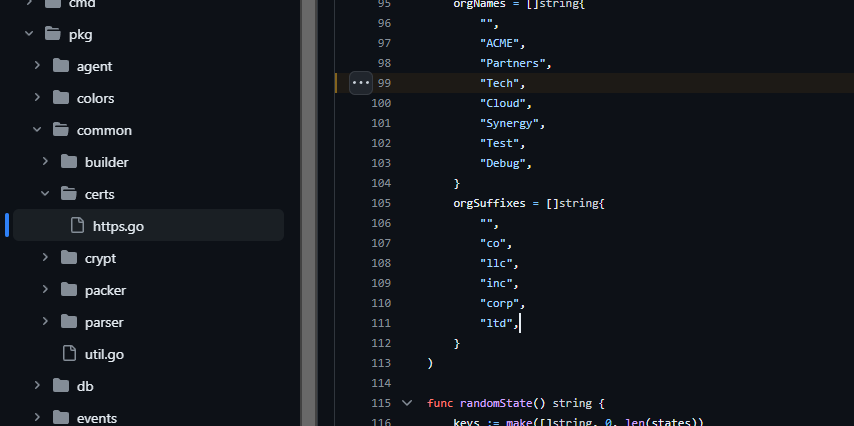
Code takes a prefix and a suffix to generate the org name. Eight options each including a null which equates to 64 potential names on certificates (inclusive of a "").
In the same file we have the IP being parsed out to the Common Name field; which unless modification is made will likely be 0.0.0.0 (we will adjust and potentially wildcard this later on though).
Looks like we might be onto something!

I love sending random things through Burp just to see how its handled. So I fired a request from my browser.


It first tries to redirect to "/home/" under a 301. Which results in a 404 with a length of 0.
So lets run a quick query in FOFA, looking for:
[+] CommonName == 0.0.0.0
[+] 301 Redirect
[+] Content length 41
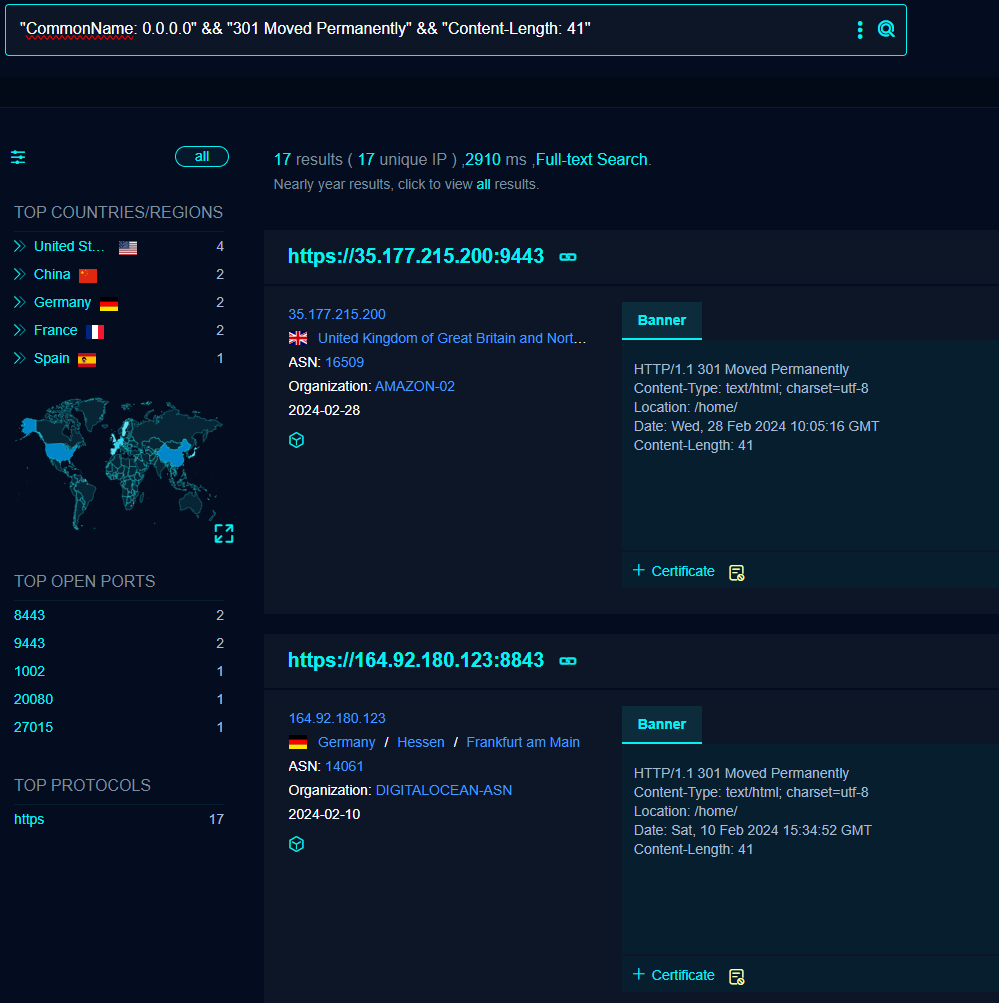

17 IP's to pick from, lets test the top two certs to validate
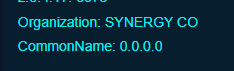
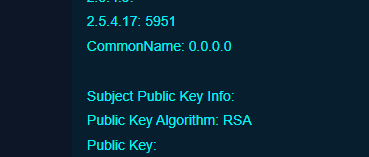
First one has two words from our known expected list. In the second one we didn't see an Organization referenced; however we know that its possible to get a null entry for that.
Pivot across to Virus Total for these two entries
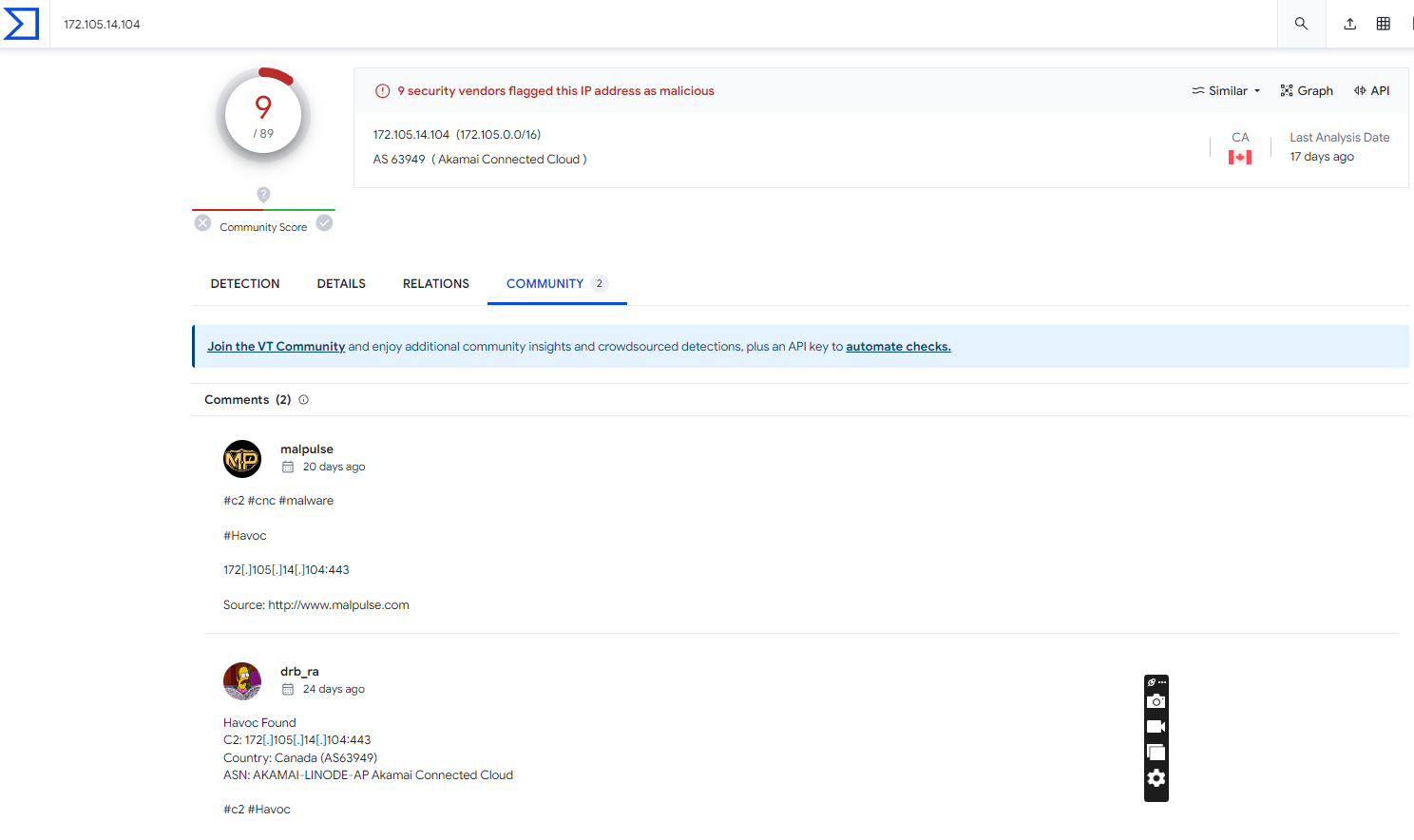
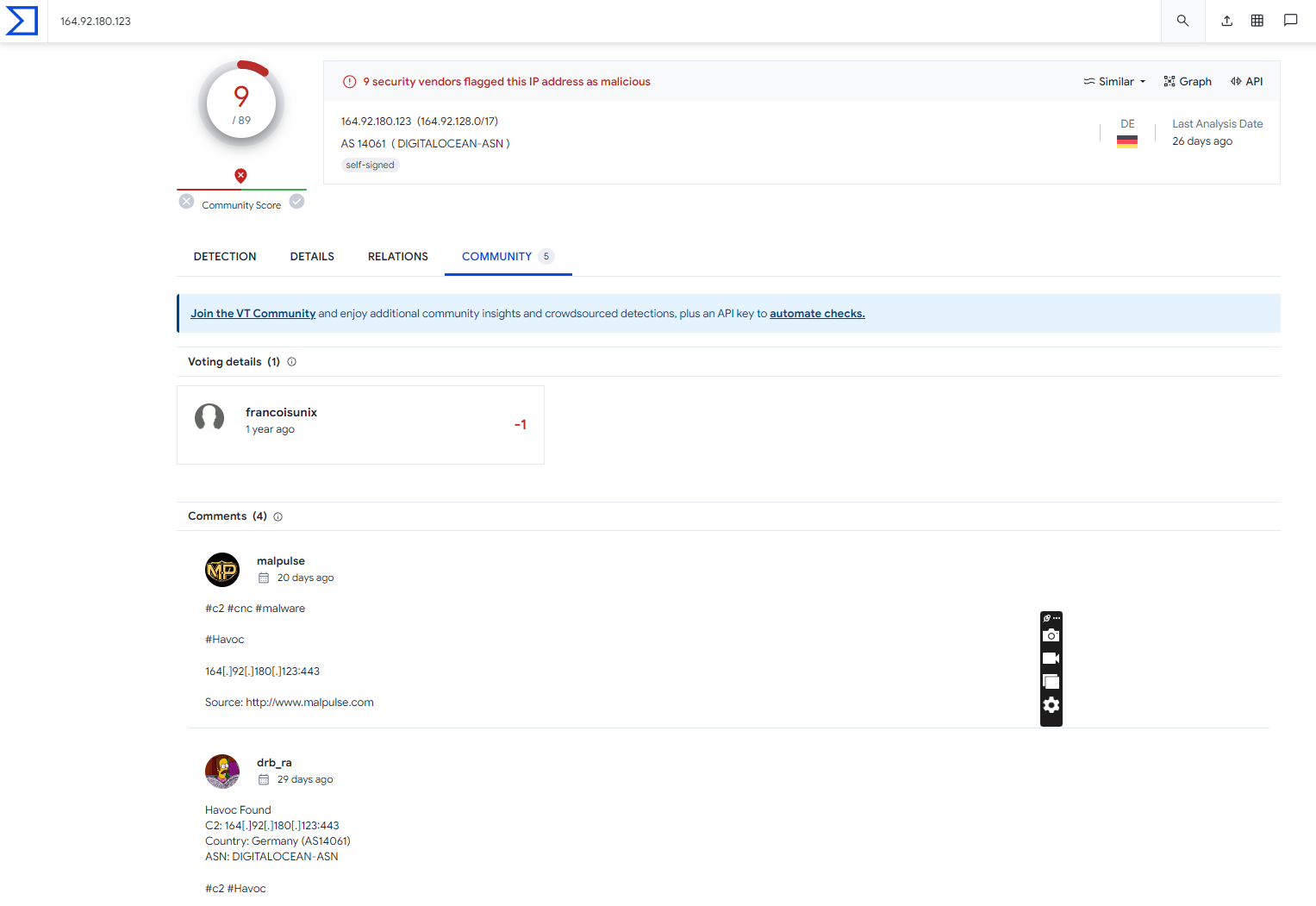
More specifically, we got 17. However as we are all likely aware, FOFA can only scan so much of the internet.

Lets shift to Censys. After a successful query which effectively searches for all variations of the certificate Org name; its clear there are some false positives with the patterns as we should see '.' and definitely not SEIKO.
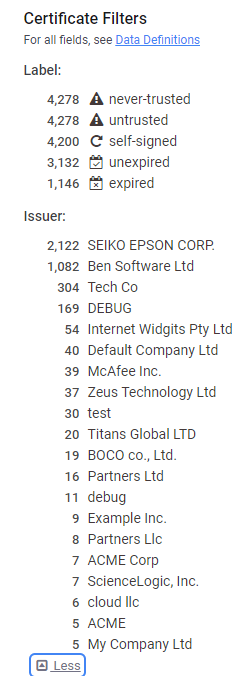
One thing our certs have that others don't is a postal/zip code; lovingly added by default within Havocs code

So the end query in Censys:
[+] Parsed common name == 0.0.0.0
[+] Postal Code exists
[+] Variation of Company name exists.
The query is pretty large as a result of using the name list for common names, so I've split it into two (See the end of this article). But this is effectively all hosts running Havoc C2 Teamserver.
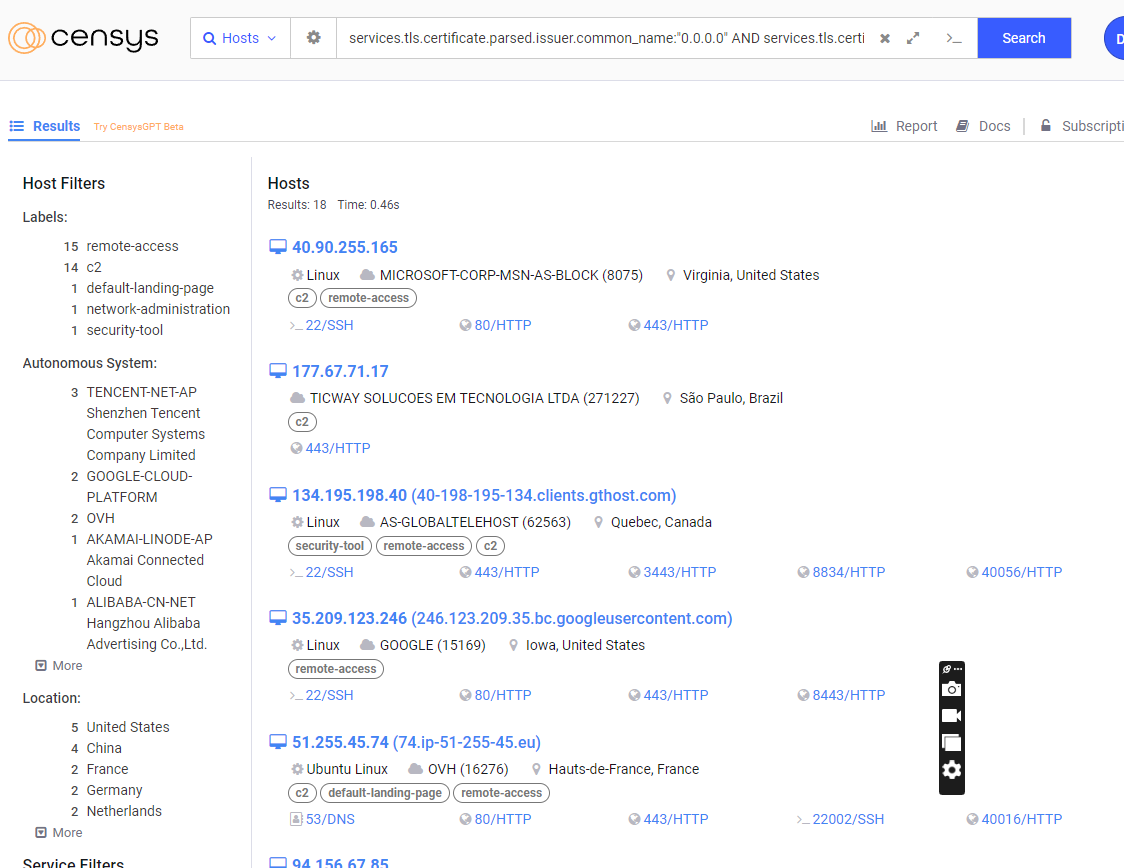
Looks promising. What I'm loving about this hunt, is that the 4th result (35.209.123[.]246) isn't tagged as a C2, which means we may have a solid indicator here.

The certificate matches the behaviour expected; unfortunately it was offline and I couldn't test directly. However a fellow hunter seems to agree in Virus Total

I see this guy seemingly every single time I'm hunting..... I don't know who you are, but fair play to you. I have questions to ask if you ever read this!

Altering the search slightly to wildcard the IP common name also proves fruitful. We find yet more untagged C2 IPs within Censys. Looking into the data we can see the Teamserver port running on a very high port number in an attempt to avoid scanners.
https://search.censys.io/hosts/84.32.188.80
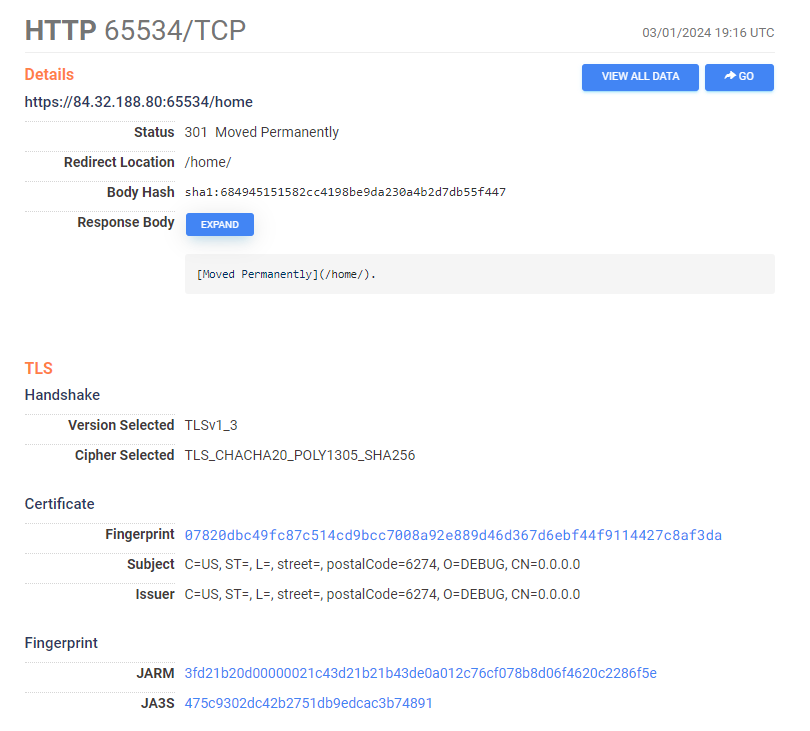
So with the altered query we find a total of 238 IPs likely running Havoc a Teamserver. of the 238, Censys only flags 70 of them.
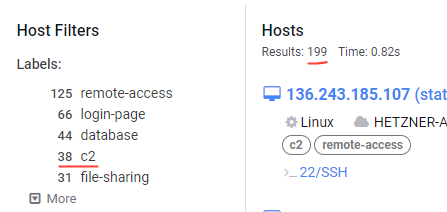
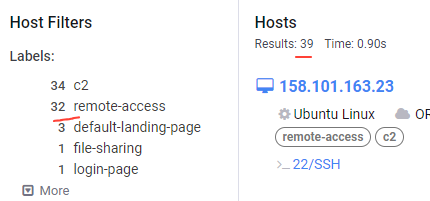
So I believe the following hunt rule to be high fidelity to detect Havoc C2 Team Servers. This is modifiable within Havoc prior to building the Team server, however it would seem this is a very common OPSEC slip up.
Fresh one running on a high port! Happy hunting!
services.tls.certificate.parsed.issuer.common_name:"*.*.*.*" AND services.tls.certificates.leaf_data.issuer.postal_code:* AND (services.tls.certificate.parsed.subject.organization:"co" OR services.tls.certificate.parsed.subject.organization:"llc" OR services.tls.certificate.parsed.subject.organization:"inc" OR services.tls.certificate.parsed.subject.organization:"corp" OR services.tls.certificate.parsed.subject.organization:"ltd" OR services.tls.certificate.parsed.subject.organization:"ACME" OR services.tls.certificate.parsed.subject.organization:"ACME co" OR services.tls.certificate.parsed.subject.organization:"ACME llc" OR services.tls.certificate.parsed.subject.organization:"ACME inc" OR services.tls.certificate.parsed.subject.organization:"ACME corp" OR services.tls.certificate.parsed.subject.organization:"ACME ltd" OR services.tls.certificate.parsed.subject.organization:"Partners " OR services.tls.certificate.parsed.subject.organization:"Partners co" OR services.tls.certificate.parsed.subject.organization:"Partners llc" OR services.tls.certificate.parsed.subject.organization:"Partners inc" OR services.tls.certificate.parsed.subject.organization:"Partners corp" OR services.tls.certificate.parsed.subject.organization:"Partners ltd" OR services.tls.certificate.parsed.subject.organization:"Tech " OR services.tls.certificate.parsed.subject.organization:"Tech co" OR services.tls.certificate.parsed.subject.organization:"Tech llc" OR services.tls.certificate.parsed.subject.organization:"Tech inc" OR services.tls.certificate.parsed.subject.organization:"Tech corp" OR services.tls.certificate.parsed.subject.organization:"Tech ltd")
services.tls.certificate.parsed.issuer.common_name:"*.*.*.*" AND services.tls.certificates.leaf_data.issuer.postal_code:* AND (services.tls.certificate.parsed.subject.organization:"Cloud " OR services.tls.certificate.parsed.subject.organization:"Cloud co" OR services.tls.certificate.parsed.subject.organization:"Cloud llc" OR services.tls.certificate.parsed.subject.organization:"Cloud inc" OR services.tls.certificate.parsed.subject.organization:"Cloud corp" OR services.tls.certificate.parsed.subject.organization:"Cloud ltd" OR services.tls.certificate.parsed.subject.organization:"Synergy " OR services.tls.certificate.parsed.subject.organization:"Synergy co" OR services.tls.certificate.parsed.subject.organization:"Synergy llc" OR services.tls.certificate.parsed.subject.organization:"Synergy inc" OR services.tls.certificate.parsed.subject.organization:"Synergy corp" OR services.tls.certificate.parsed.subject.organization:"Synergy ltd" OR services.tls.certificate.parsed.subject.organization:"Test " OR services.tls.certificate.parsed.subject.organization:"Test co" OR services.tls.certificate.parsed.subject.organization:"Test llc" OR services.tls.certificate.parsed.subject.organization:"Test inc" OR services.tls.certificate.parsed.subject.organization:"Test corp" OR services.tls.certificate.parsed.subject.organization:"Test ltd" OR services.tls.certificate.parsed.subject.organization:"Debug " OR services.tls.certificate.parsed.subject.organization:"Debug co" OR services.tls.certificate.parsed.subject.organization:"Debug llc" OR services.tls.certificate.parsed.subject.organization:"Debug inc" OR services.tls.certificate.parsed.subject.organization:"Debug corp" OR services.tls.certificate.parsed.subject.organization:"Debug ltd")