Hunting For Sliver C2 Servers With FOFA
How we can use FOFA to identify indicators to hunt for Sliver C2 instances running multiplayer

Sliver is a C2 framework made by the guys at Bishop Fox. The github repo can be found here. As a brief overview, Sliver would run on a server allowing for "Players" (attackers) to connect to the multiplayer server and administer commands collaboratively to victims running the beacon/implant payload.
This article is not to identify these payloads; it is to go out of our own perimeters and search online for existing servers.
Hypothesis
Where do we start?
Looking at the installation guide available via Dominic Breuker, we can see that a novel port of 31337 is in use.
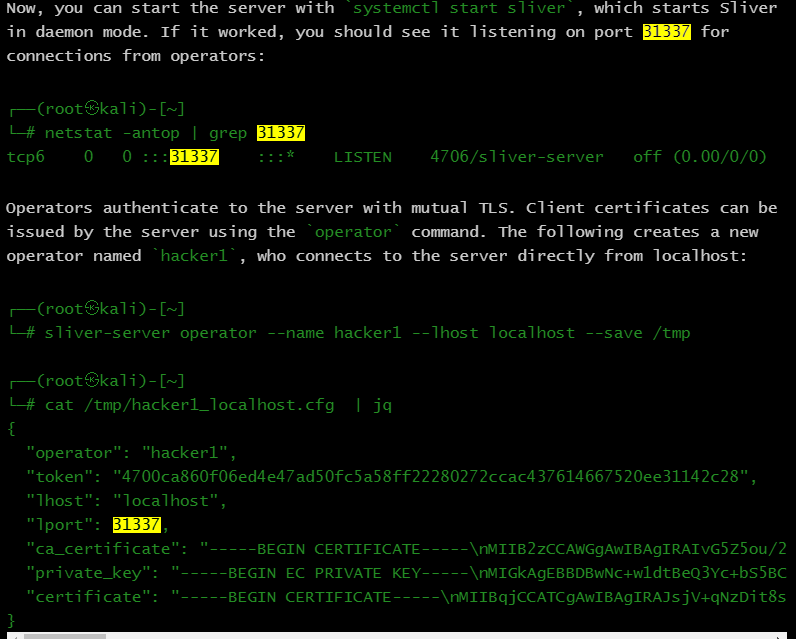
Now, this is not necessarily a default port, but many will likely use default installation guides. So lets look for a known Sliver C2.
Finding A Bad Server To Look At
Via threatfox's feed, we can identify an active Sliver C2

You'll see lots of references to the port 31337. For this example I've shifted to FOFA using IP 51.210.178.238, a Sliver C2 active on OVH SAS in France.
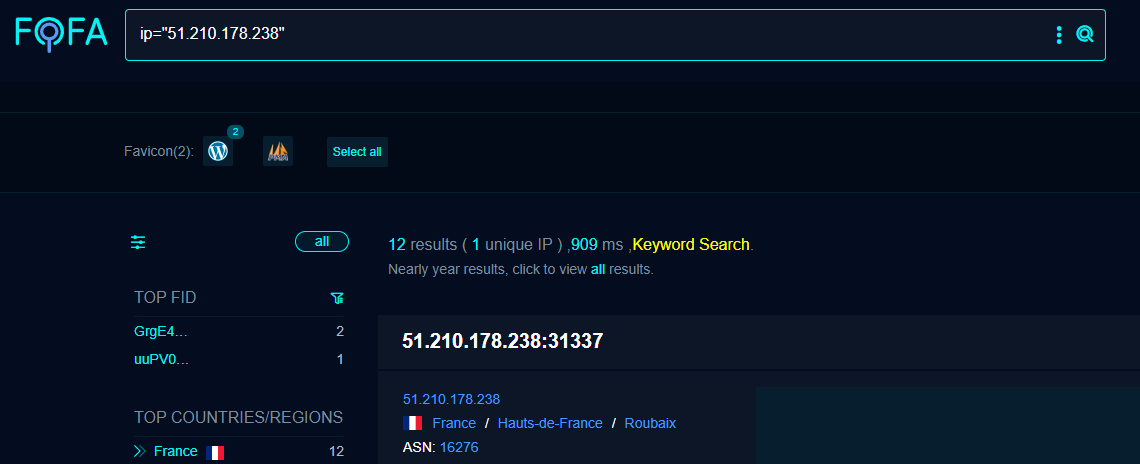
First (and only) Pivot
Expanding the certificate field for port 31337 we find some pretty good information to pivot on...
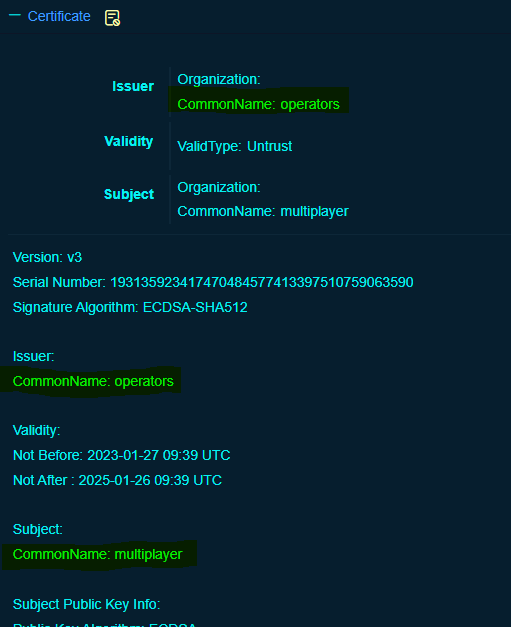
"Operators" and "Multiplayer" should not be common names for certificates. Pivoting on this we can open up a search for where these two strings exist:
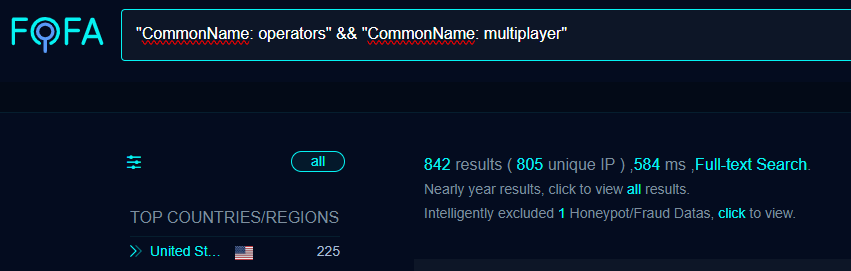
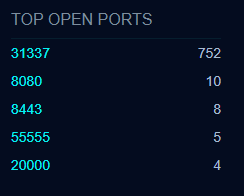
842 results, including variations in the default port being used:
Randomised Validation
Checking we didnt just find garbage
Delving into one of the results we can see the there is a content-length of '0' via a 404 on port 443, a common indicator of Cobalt Strike and Sliver being active. To add to this the certificate also matches the pattern.
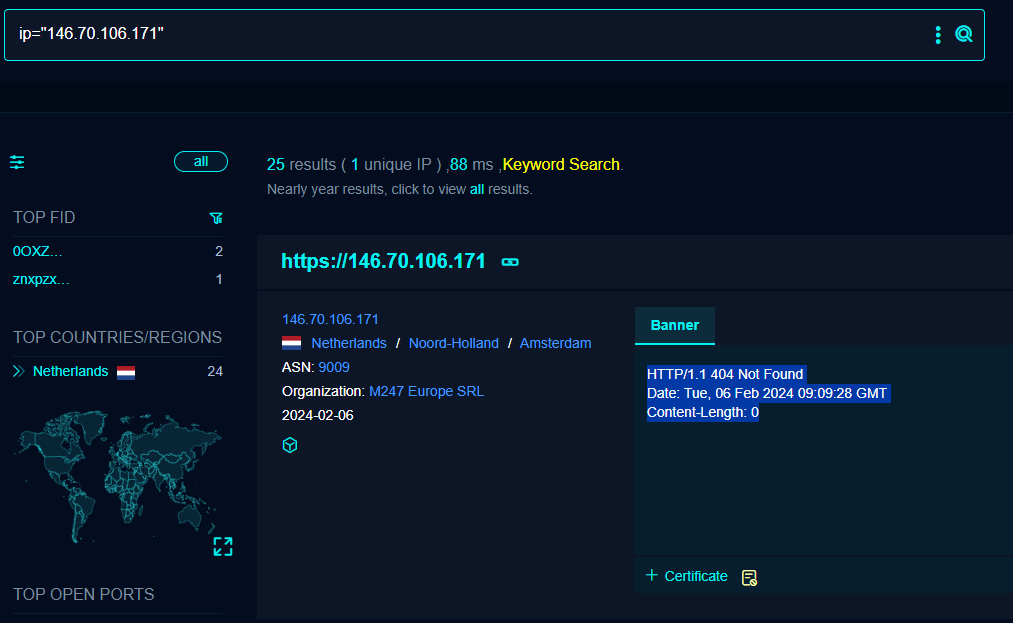
Suffice to say this is not all Sliver servers, but a fair indicator to hunt on.
Summary
TLDR;
Within FOFA searching for the following should result in showing servers that have been configured to run the players port globally. FOFA seems to detect this better than Shodan, not sure why.
Search Query: "CommonName: operators" && "CommonName: multiplayer"