Hunting For the 'Contiinued' Phish Kit
We pick up something from the trash pile and figure out its phish kit family! Giving birth to a hunt query to detect Contiinued phish kit portals using URLScan
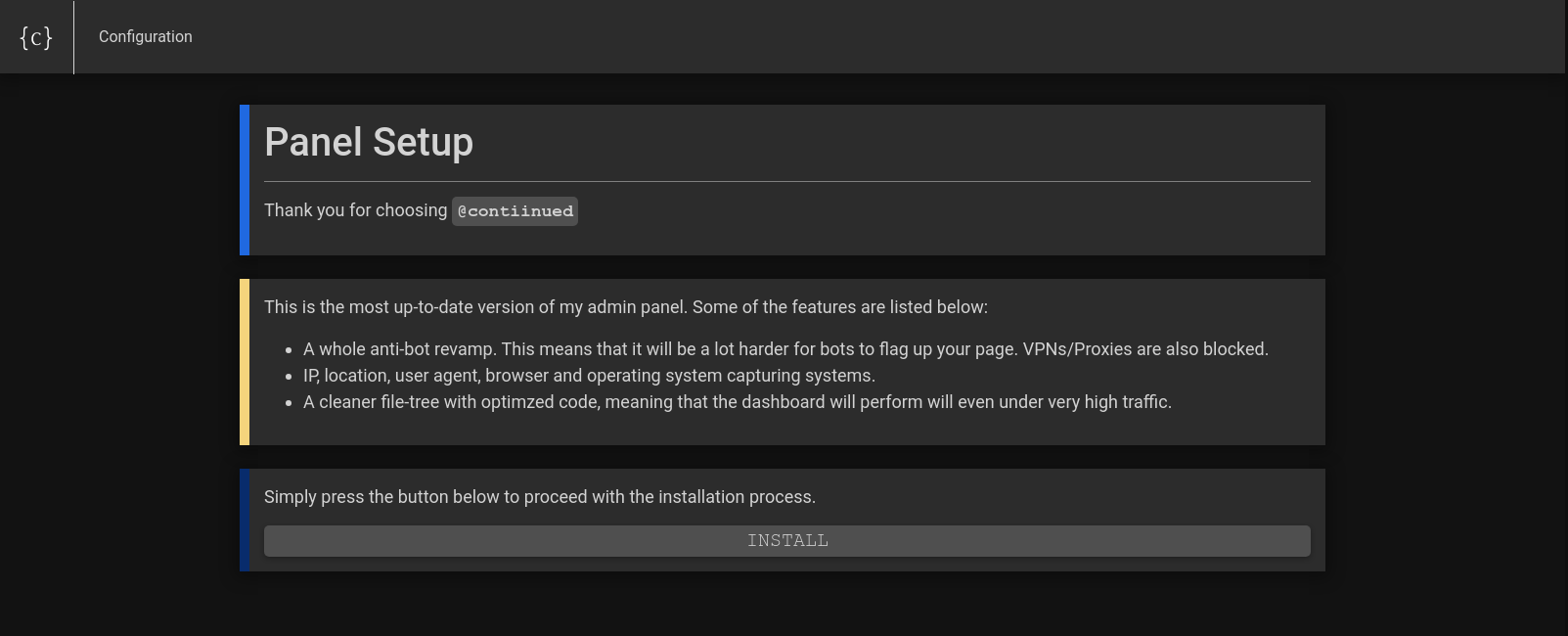
So today... we will be dissecting the shit out of a fraud page; and figuring out how to map it to its originating phishing kit. Succeeding that, we will have a nice indicator to spot and tag them accordingly and maybe have some fun with the functionality on the way. Spoiler alert: Its 'Contiinued' as specified in the title.
The site in question we will be looking at is "commerzbankeinloggen.com/pages" in which the URLScan output we will be assessing is here.
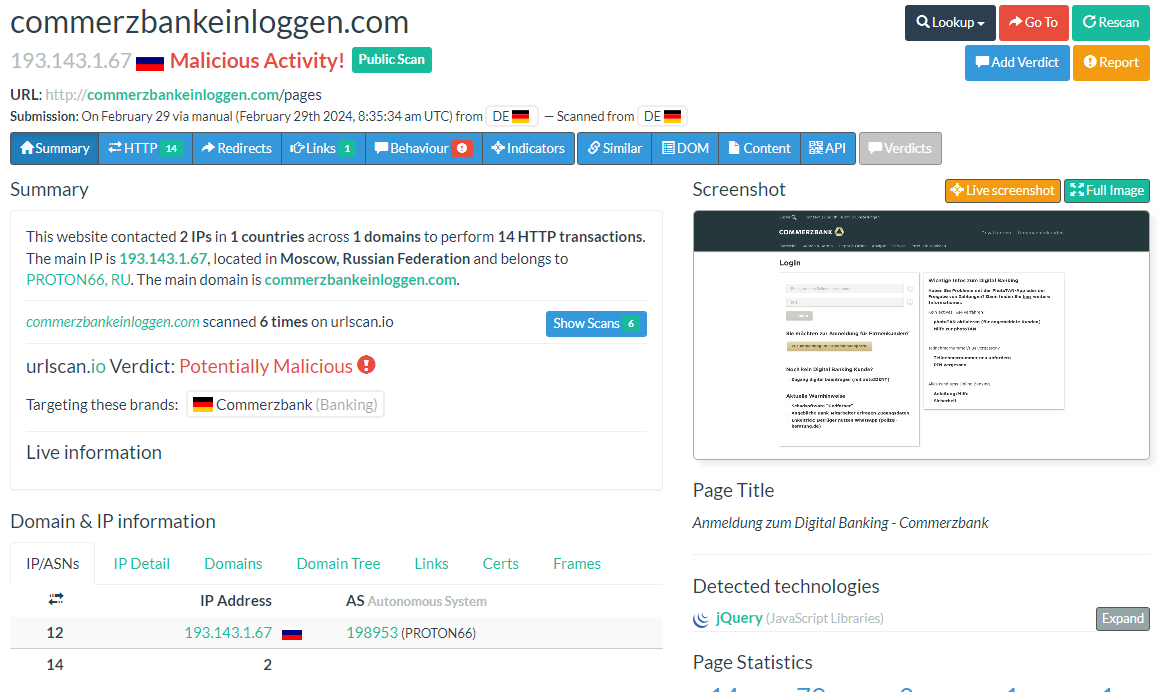
So URLScan already sees this is bad...

Where we will find the start of our hunt, is viewing the code structure of the page:

Key thing I'm looking for within the HTML is "unique" behaviour. This can be hashes of images, files loaded etc. One does catch my eye...
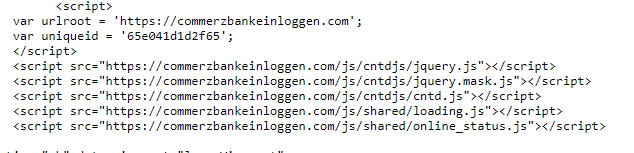
A load of JavaScript's loaded from a particular path /js/cntdjs/'.
This could well be a static indicator in its own right without having to pivot to files hashes. Search query within URLScan to look for filenames...
filename:"/js/cntdjs/*"
This displays an array of fraud!!!
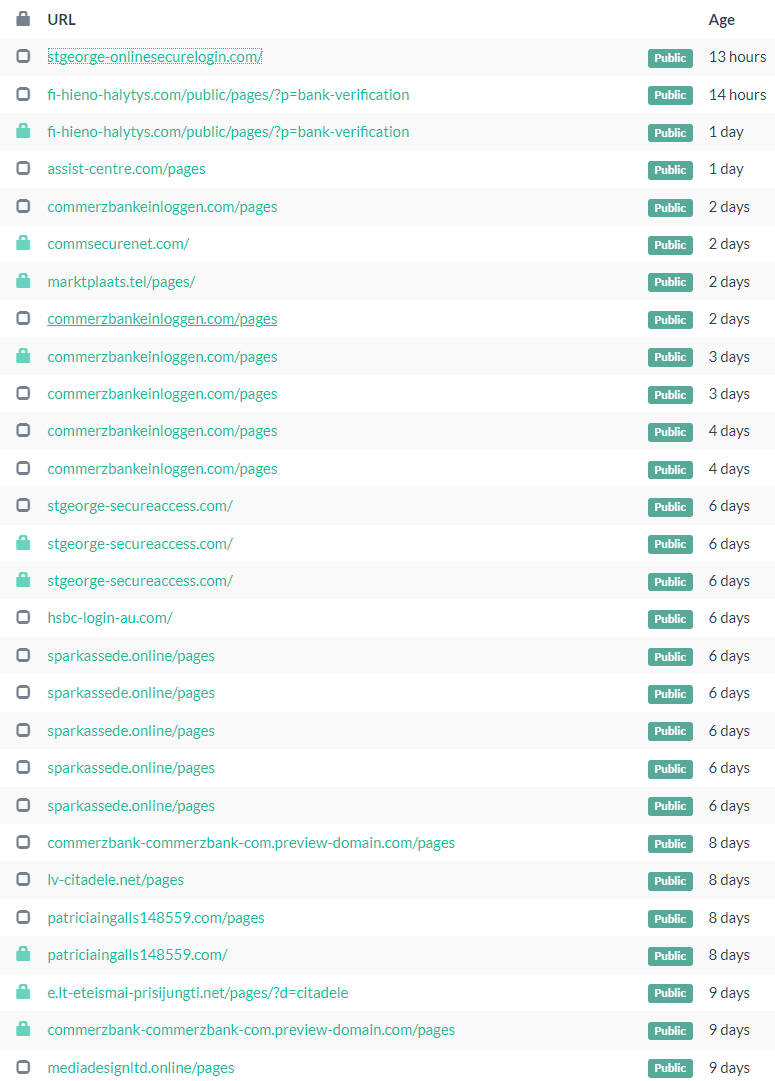

They're all fairly phishy. So I spend some time going through them... only to find this...
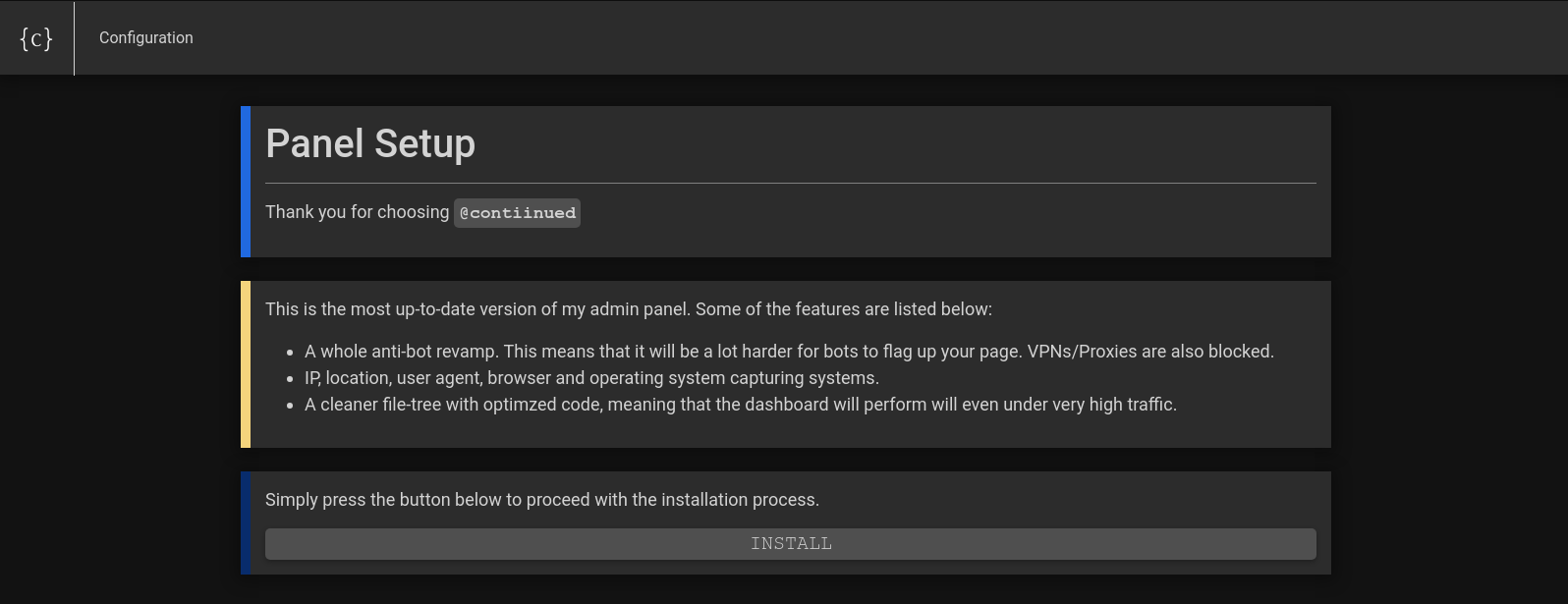

The phisher didn't even have time to configure his panel prior to launching the campaign... we now know this is the 'Contiinued' phish kit. This is what I look for as much as I can. OPSEC fails give us opportunity as hunters to pivot and reveal extra information that we really shouldn't be able to correlate.
Browsing around the web I wanted to know more about this kit. I've since found an amazing article whereby someone YOLO'd their way onto the infrastructure. I say YOLO it was more of a Leeroy Jenkins moment for those of you who remember those days.

He goes on to explain the panel layout of the kit after its been witnessed first hand. Well worth a read!

I havent not validated the findings of the article by Saraunsh0x9; but have little reason to disbelieve it.
Want to look at Contiinued yourself? Try this search and dig in